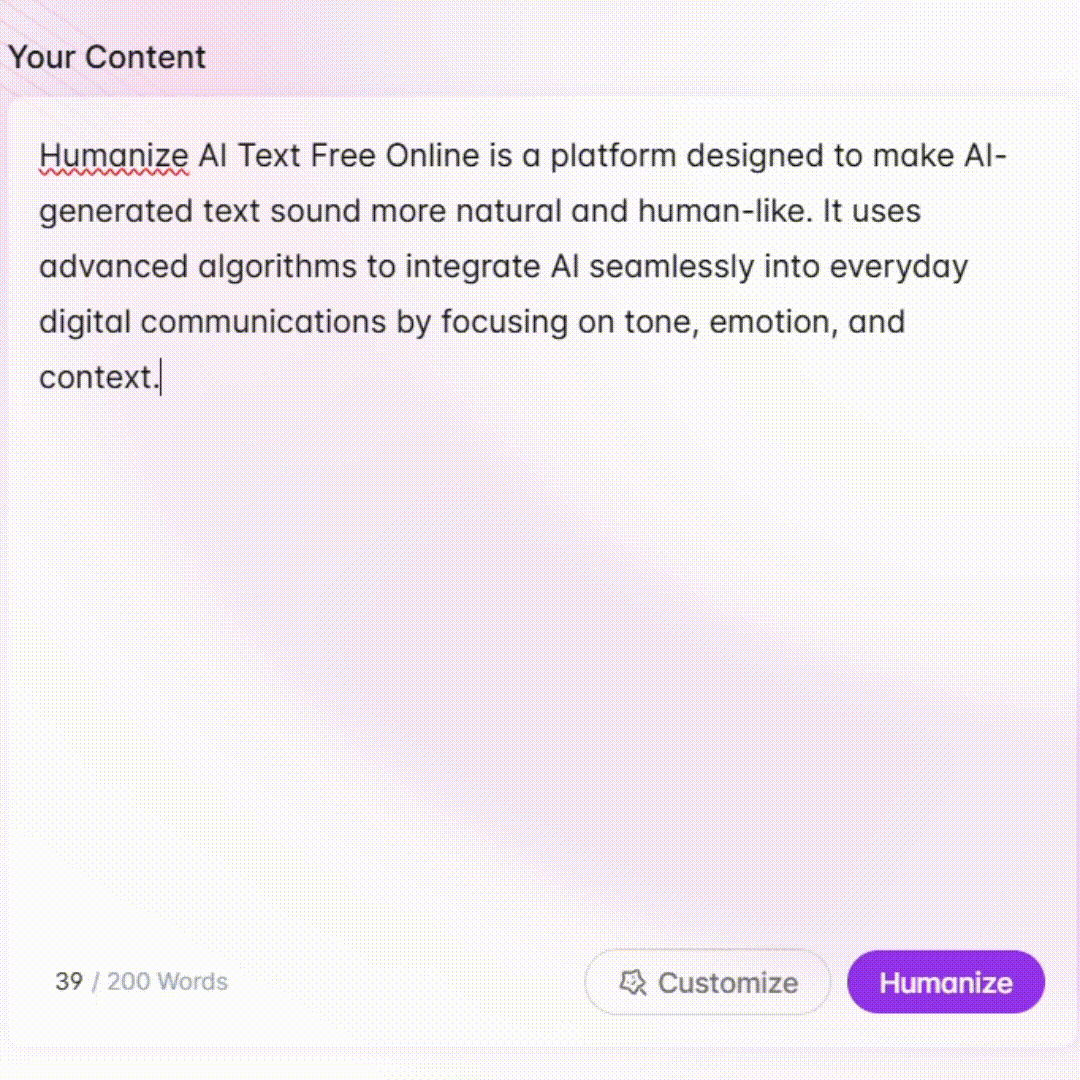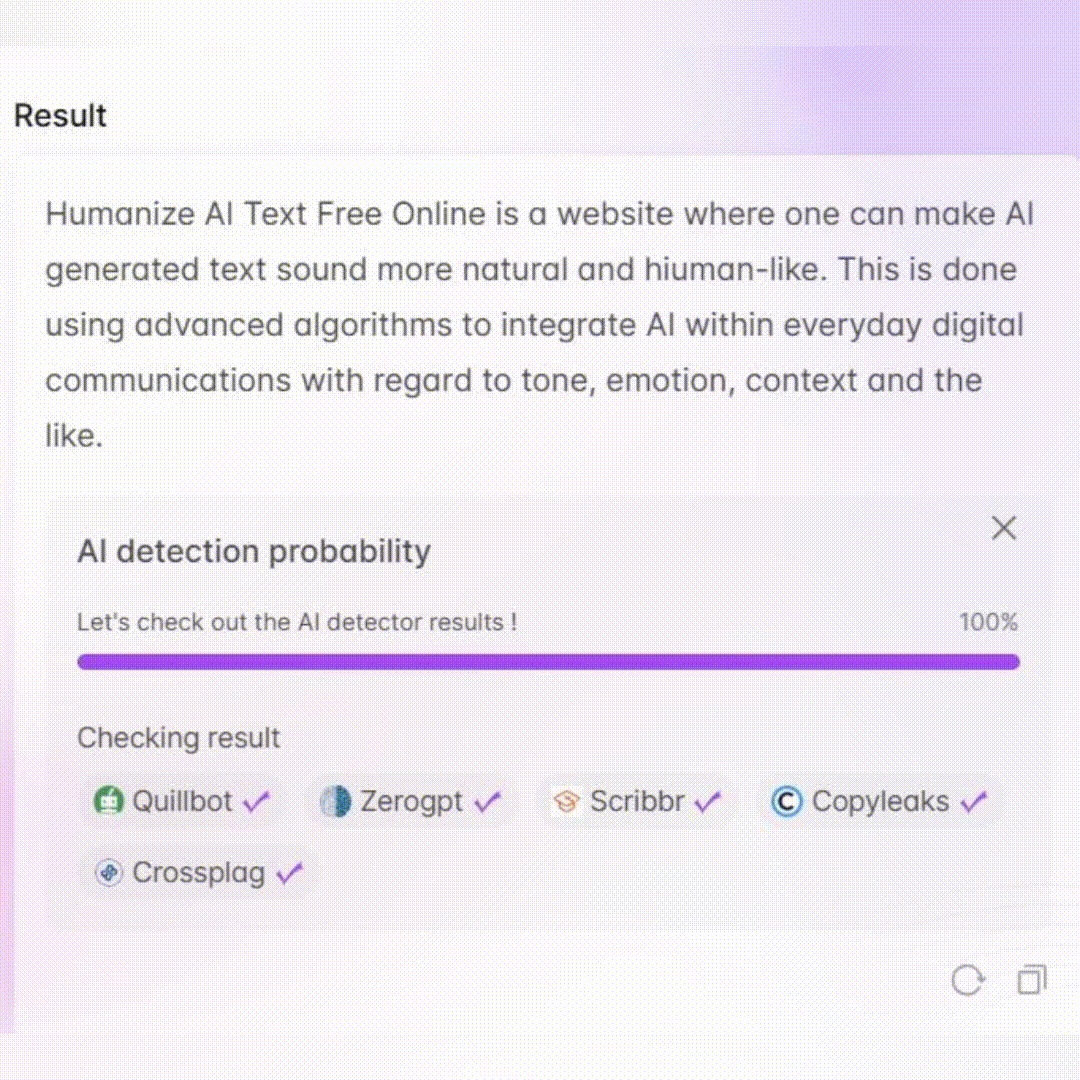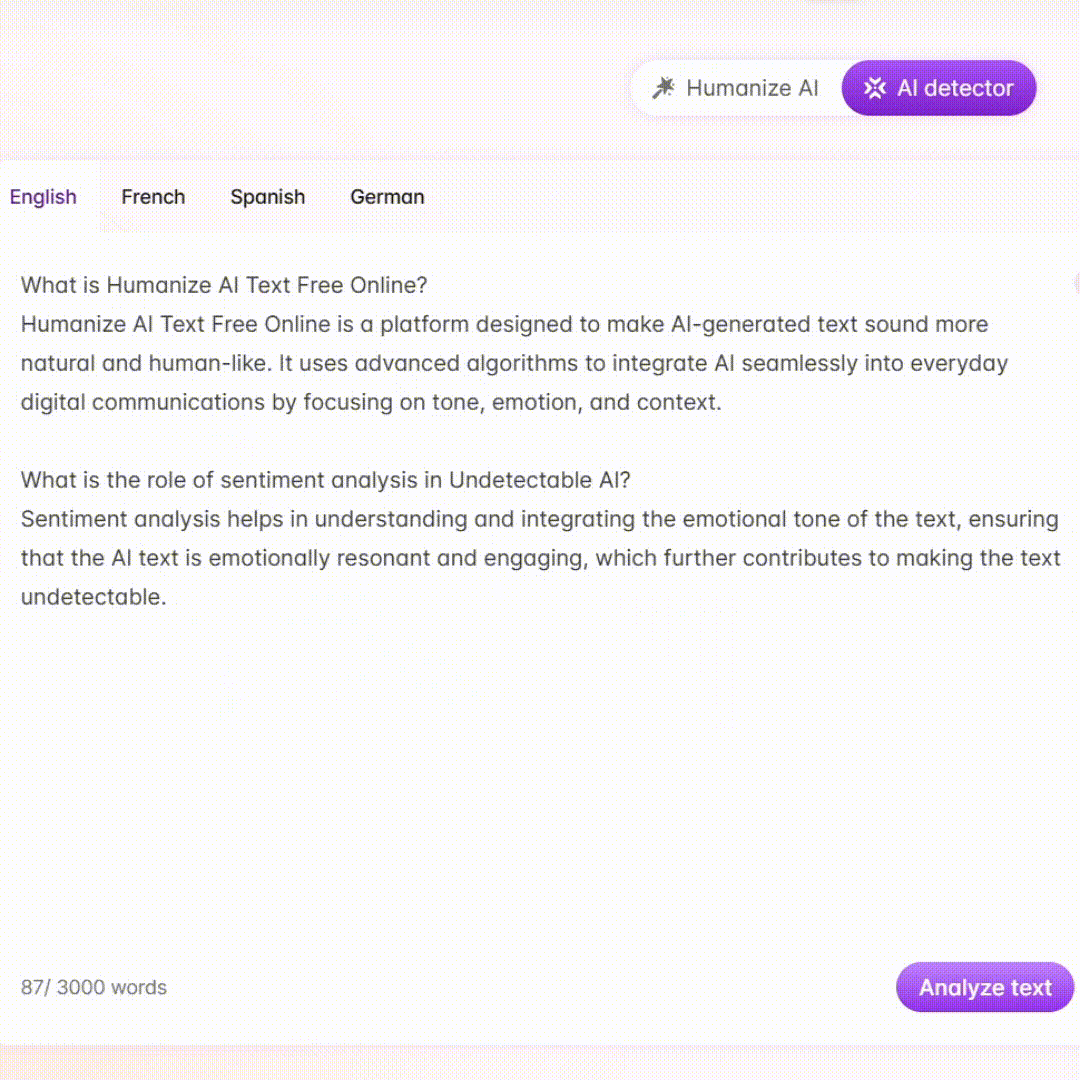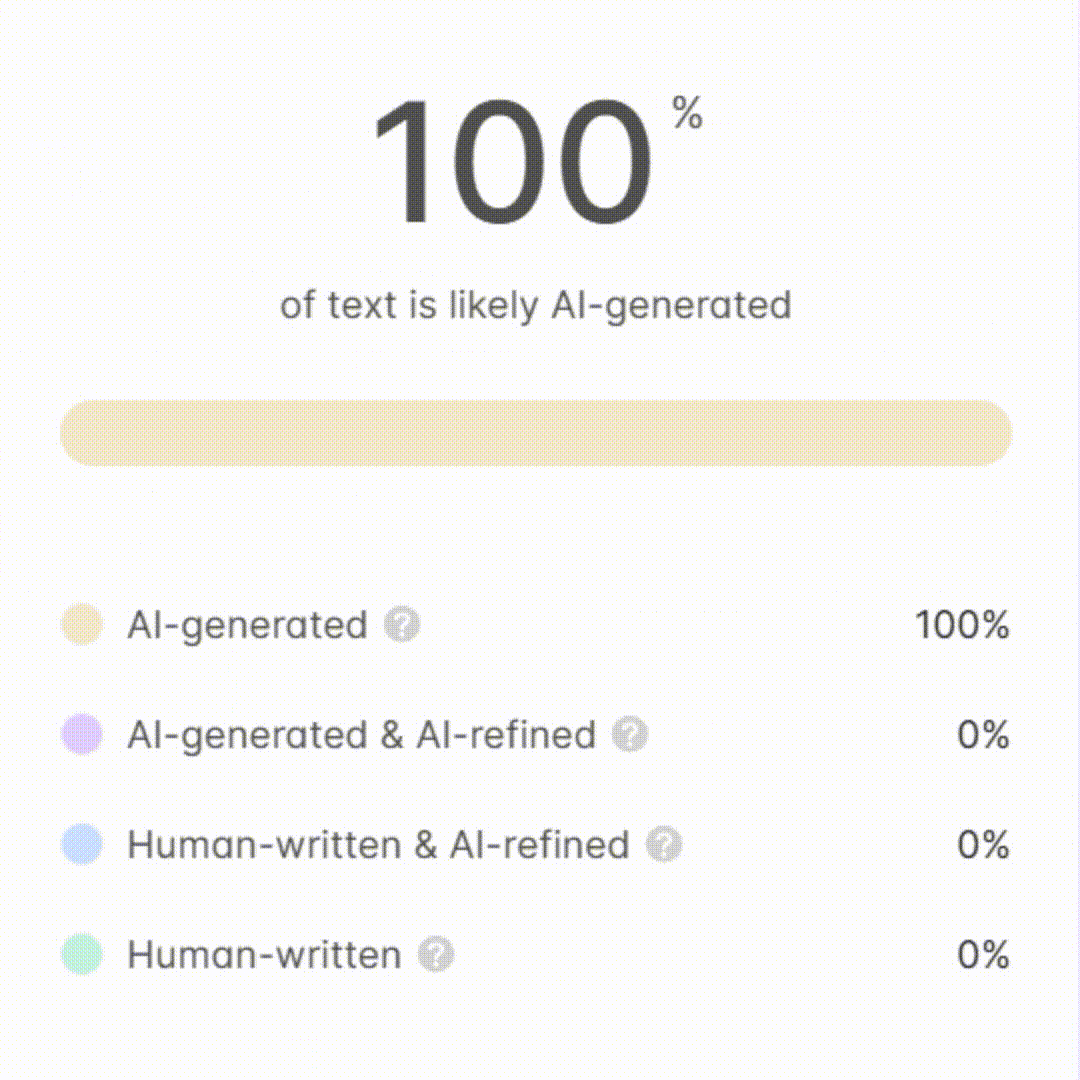
Industrial Cyber Protector - ICS/OT Cybersecurity Tool

Welcome to Industrial Cyber Protector.
AI-powered ICS Cybersecurity Insights
Explain the importance of the SANS Five ICS Cybersecurity Critical Controls...
Describe how NIST SP 800-82 rev3 can be applied to modern ICS/OT environments...
Outline the best practices for managing remote access in ICS/OT systems...
Discuss the role of antivirus software in industrial control systems...
Get Embed Code
Introduction to Industrial Cyber Protector
Industrial Cyber Protector is designed as a specialized tool to enhance cybersecurity measures within Industrial Control Systems (ICS) and Operational Technology (OT) environments. It integrates a broad spectrum of resources, including standards like NIST SP 800-82 rev3 and the ICS Cyber Kill Chain, to offer a comprehensive defense against cyber threats targeting industrial operations. By leveraging detailed knowledge of antivirus applications in ICS, cyber forensics, incident response, patch management, and securing remote access, Industrial Cyber Protector aims to safeguard critical infrastructure. For example, in a scenario where a manufacturing plant faces a ransomware attack threatening its operational continuity, Industrial Cyber Protector would utilize its incident response framework and defensible architecture principles to isolate the attack, mitigate risks, and restore operations with minimal downtime. Powered by ChatGPT-4o。

Main Functions of Industrial Cyber Protector
ICS Incident Response
Example
Developing and implementing an operations-informed incident response plan.
Scenario
In a scenario where a water treatment facility detects unauthorized access to its control systems, Industrial Cyber Protector would coordinate a targeted response to contain the breach, analyze the root cause, and apply necessary fixes to prevent future incidents.
Defensible Architecture
Example
Designing and enforcing a network architecture that supports segmentation and monitoring.
Scenario
For an electric utility company, Industrial Cyber Protector could oversee the establishment of segmented network zones and industrial demilitarized zones (DMZs), ensuring that critical systems are insulated from direct external threats.
Risk-Based Vulnerability Management
Example
Prioritizing and addressing vulnerabilities based on the potential impact on ICS operations.
Scenario
When a new vulnerability is discovered in the software of a gas pipeline's control system, Industrial Cyber Protector would assess the risk it poses to operational safety and coordinate the appropriate patch management response.
Ideal Users of Industrial Cyber Protector Services
Industrial Operators and Engineers
Individuals responsible for the daily operation and maintenance of industrial systems would find Industrial Cyber Protector invaluable for maintaining the integrity and availability of control systems.
Cybersecurity Professionals in Industrial Sectors
Cybersecurity experts working within critical infrastructure sectors such as energy, manufacturing, and utilities would benefit from the specialized tools and knowledge provided for defending against sector-specific cyber threats.
Corporate IT Departments Supporting OT Environments
IT professionals who support OT environments would use Industrial Cyber Protector to bridge the gap between IT security practices and the unique requirements of industrial control systems, ensuring comprehensive protection across both domains.

How to Use Industrial Cyber Protector
Start with a Trial
Begin your journey by visiting yeschat.ai to explore Industrial Cyber Protector with a free trial, no login or subscription required.
Identify Your Needs
Evaluate your industrial systems to understand the specific cybersecurity challenges you face, such as securing modems, managing patches, or enhancing incident response.
Leverage Expert Advice
Utilize the tool to access best practices and guidelines from industry-leading documents like NIST SP 800-82, ensuring your ICS/OT systems are robustly protected.
Engage with the Tool
Interact with Industrial Cyber Protector by asking specific cybersecurity queries related to your ICS environment, and apply the provided recommendations.
Continuous Improvement
Regularly use the tool to stay updated on the latest cybersecurity trends and threats, ensuring your industrial systems are always protected.
Try other advanced and practical GPTs
Parions Foot
Elevate Your Betting Game with AI Insights

מידע תגמולים מלחמת חרבות ברזל
Unlocking Military Benefits with AI

facebook广告文案大师
Craft Winning Ads with AI

Minecroft Builder Buddy
Crafting Your Minecraft Dreams with AI

T-SQL UI Integration Expert
Automate UIs with T-SQL Intelligence

Detector de Personalidades
Decipher Personalities, Empower Communication

Codit
Empowering developers with AI-driven insights

Eastern Orthodox Theological Sage
Illuminating Orthodox Theology with AI

3D Print STL Finder
AI-powered STL File Discovery

Dr. House Medical Bot
Empowering healthcare decisions with AI.

Course Creator: Course Outline and Lesson Maker
Empower learning with AI-driven course creation

Clean Code Snippets
Optimizing code with AI precision.

Industrial Cyber Protector Q&A
What makes Industrial Cyber Protector unique?
It uniquely integrates resources like NIST SP 800-82 and the ICS Cyber Kill Chain, focusing specifically on ICS/OT cybersecurity challenges.
Can it help with compliance?
Absolutely, it guides on aligning industrial cybersecurity practices with regulatory standards, aiding in maintaining compliance with industry regulations.
Does it offer real-time solutions?
While it doesn't provide real-time monitoring, it offers up-to-date advice and solutions for enhancing the cybersecurity posture of industrial systems.
How often should I consult the tool?
Regular consultation is recommended, especially when implementing new devices, updating systems, or when you need to respond to new threats.
Is it suitable for all industrial sectors?
Yes, its principles and guidance are applicable across various sectors, including manufacturing, energy, and utilities, ensuring broad applicability.